Questions
1. What is the image hash? Does the acquisition and verification hash match?
2. What operating system was used on the computer?
root@kali:/mnt/2to/nist# file image.dd
image.dd: x86 boot sector, Microsoft Windows XP MBR, Serial 0xec5dec5d; partition 1: ID=0x7, active, starthead 1, startsector 63, 9510417 sectors, code offset 0xc0
root@kali:/mnt/2to/nist# mmls image.dd
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
00: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
01: ----- 0000000000 0000000062 0000000063 Unallocated
02: 00:00 0000000063 0009510479 0009510417 NTFS (0x07)
03: ----- 0009510480 0009514259 0000003780 Unallocated
- Montage de l'image:
L'unité du offset de mount est en octets.
root@kali:/mnt/2to/nist# bc bc 1.06.95 Copyright 1991-1994, 1997, 1998, 2000, 2004, 2006 Free Software Foundation, Inc. This is free software with ABSOLUTELY NO WARRANTY. For details type `warranty'. 63*512 32256 quit root@kali:/mnt/2to/nist# mount -o loop,offset=32256 image.dd /mnt/image/
3. When was the install date?
Rappel sur les fichiers contenant les hives: Sauf pour les profils des users NTUSSER.DAT(documents and settings/…), les fichiers se trouvent dans windows/system32/config
Default : HKEY_USERS\.Default SAM : HKEY_LOCAL_MACHINE\SAM Security : HKEY_LOCAL_MACHINE\Security Software : HKEY_LOCAL_MACHINE\Software System : HKEY_LOCAL_MACHINE\System NTUSER.DAT : KKEY_CURRENT_USER
root@kali:/mnt/2to/nist/registre# hivexsh software
Bienvenue dans hivexsh, l'interpréteur de commandes interactif hivex pour examiner
les fichiers « hive » du registre Windows.
Tapez: « help » pour un résumé de l'aide
« quit » pour quitter l'interpréteur de commandes
software\> cd Microsoft
software\Microsoft> cd Windows NT
software\Microsoft\Windows NT> cd CurrentVersion
software\Microsoft\Windows NT\CurrentVersion> lsval
"CurrentBuild"="1.511.1 () (Obsolete data - do not use)"
"InstallDate"=dword:41252e3b
"ProductName"="Microsoft Windows XP"
"RegDone"=""
"RegisteredOrganization"="N/A"
"RegisteredOwner"="Greg Schardt"
"SoftwareType"="SYSTEM"
"CurrentVersion"="5.1"
"CurrentBuildNumber"="2600"
"BuildLab"="2600.xpclient.010817-1148"
"CurrentType"="Uniprocessor Free"
"SystemRoot"="C:\\WINDOWS"
"SourcePath"="D:\\"
"PathName"="C:\\WINDOWS"
"ProductId"="55274-640-0147306-23684"
"DigitalProductId"=hex(3):a4,00,00,00,03,00,00,00,35,35,32,37,34,2d,36,34,30,2d,30,31,34,37,33,30,36,2d,32,33,36,38,34,00,2e,00,00,00,41,32,32,2d,30,30,30,30,31,00,00,00,00,00,00,00,14,b3,4b,cc,f7,44,da,3a,75,65,93,26,b6,f4,00,00,00,00,00,00,f1,dc,24,41,cc,b2,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,35,35,32,30,30,00,00,00,00,00,00,00,94,10,00,00,9b,8d,b1,6c,80,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,c8,7b,fc,7c
"LicenseInfo"=hex(3):34,54,ae,dc,c7,2e,3d,e5,8b,15,06,1a,8c,74,a6,55,8c,9b,49,a9,3f,24,2b,04,44,ef,79,88,c1,32,38,cf,52,0c,d7,57,da,9b,35,aa,d9,44,b3,64,b9,21,6d,76,74,56,d2,4e,91,6e,7f,ac
Conversion:
# echo 'ibase=16;obase=A;41252E3B' | bc 1092955707 # date -d @1092955707 +'%d/%m/%Y (%A) at %X (UTC %:z)' 20/08/2004 (vendredi) at 00:48:27 (UTC +02:00)
4. What is the timezone settings?
system\ControlSet001\Control\TimeZoneInformation> lsval "Bias"=dword:00000168 "StandardName"="Central Standard Time" "StandardBias"=dword:00000000 "StandardStart"=hex(3):00,00,0a,00,05,00,02,00,00,00,00,00,00,00,00,00 "DaylightName"="Central Daylight Time" "DaylightBias"=dword:ffffffc4 "DaylightStart"=hex(3):00,00,04,00,01,00,02,00,00,00,00,00,00,00,00,00 "ActiveTimeBias"=dword:0000012c
- Les clés “Bias” et “ActiveTimeBias” ont pour unités la minute:
BIAS: # echo 'ibase=16;168' | bc 360 <=> 6 heures ActiveTimeBias: # echo 'ibase=16;12C' | bc 300 <=> 5 heures
- Les clés “StandardStart” et “DaylightStart” sont à convertir comme suit:
Elles devraient correspondre à la structure SYSTEMTIME,mais il y a un décalage.
Exemple:
"DaylightStart"=hex(3):00,00,04,00,01,00,02,00,00,00,00,00,00,00,00,00 00 = ? 00 = year 04 = mois, Avril 00 = Jour de la semaine, Dimanche=0 01 = Première semaine, 05 étant la dernière 00 = ? 02 = Heure, 2 Heure du matin 00 = Minute 00 = Sec 00 = ms
- La clé DaylightBias se calcule comme suit:
1) # echo 'ibase=16;obase=2;FFFFFFC4' | bc
11111111111111111111111111000100
2) Le bit de poids fort étant à 1, la valeur de cette clef sera négative. On inverse les bits:
111011
3) On ajoute 1 à cette valeur:
111011+1=00111100
en decimal:
-60
Si la valeur était positive, on n'aurait pas eu besoin de rajouter 1.
5. Who is the registered owner?
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion ... "RegisteredOwner"="Greg Schardt" ...
6. What is the computer account name?
system\ControlSet001\Control\ComputerName\ComputerName> lsval "ComputerName"="N-1A9ODN6ZXK4LQ"
7. What is the primary domain name?
Listing des interfaces réseaux:
system\ControlSet001\Control\Class\{4D36E972-E325-11CE-BFC1-08002bE10318}\\0010> lsval
"Configured"="1"
"DriverVariant"="1"
"DriverMajor"="7"
"DriverMinor"="14"
"DesiredSSID"="Agere Systems"
"VendorDescription"="ORINOCO PC Card"
"Characteristics"=dword:00000084
"BusType"="8"
"ComponentId"="pcmcia\\compaq-compaq_wl110_pc_card-e648"
"OwnChannel"="0"
"OwnName"=""
"PMEnabled"="0"
"TxRateControl"="3"
"InfPath"="netwv48.inf"
"InfSection"="wlluc48.Install"
"ProviderName"="Microsoft"
"DriverDateData"=hex(3):00,80,62,c5,c0,01,c1,01
"DriverDate"="7-1-2001"
"DriverVersion"="7.14.0.1"
"MatchingDeviceId"="pcmcia\\compaq-compaq_wl110_pc_card-e648"
"DriverDesc"="Compaq WL110 Wireless LAN PC Card"
"NetCfgInstanceId"="{86FC0C96-3FF2-4D59-9ABA-C602F213B5D2}"
Sous w7, l'adresse MAC est donnée par la clé BIMacAddress:
Dans l'exemple suivant, l'adresse MAC sera :
BIMacAddress_h+BIMacAddress_l=0022157383a4
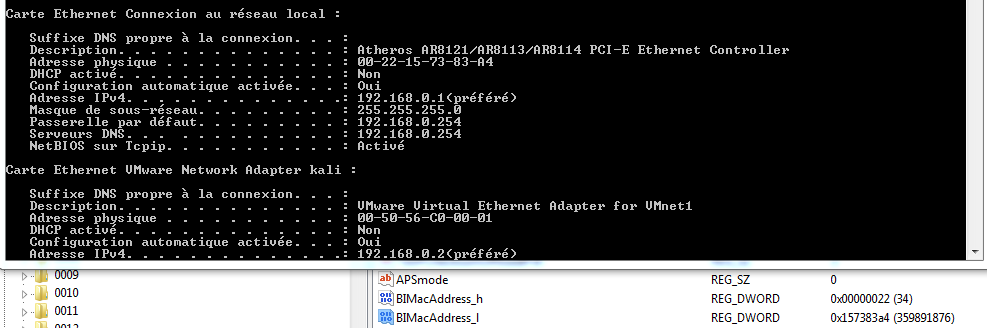 Sous XP, 2000 la clé est NetworkAddress, elle n'est pas présente dans cet exemple.
Sous XP, 2000 la clé est NetworkAddress, elle n'est pas présente dans cet exemple.
L'adresse MAC peut être trouvée dans les fichiers de logs, voir question 14.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkCards
software\Microsoft\Windows NT\CurrentVersion> cd networkCards
software\Microsoft\Windows NT\CurrentVersion\NetworkCards> ls
11
2
software\Microsoft\Windows NT\CurrentVersion\NetworkCards> lsval
software\Microsoft\Windows NT\CurrentVersion\NetworkCards> cd 11
software\Microsoft\Windows NT\CurrentVersion\NetworkCards\11> ls
software\Microsoft\Windows NT\CurrentVersion\NetworkCards\11> lsval
"ServiceName"="{86FC0C96-3FF2-4D59-9ABA-C602F213B5D2}"
"Description"="Compaq WL110 Wireless LAN PC Card"
software\Microsoft\Windows NT\CurrentVersion\NetworkCards\11> cd ..
software\Microsoft\Windows NT\CurrentVersion\NetworkCards> cd 2
software\Microsoft\Windows NT\CurrentVersion\NetworkCards\2> ls
software\Microsoft\Windows NT\CurrentVersion\NetworkCards\2> lsval
"ServiceName"="{6E4090C2-FAEF-489A-8575-505D21FC1049}"
"Description"="Xircom CardBus Ethernet 100 + Modem 56 (Ethernet Interface)"
system\ControlSet001\Services\Tcpip\Parameters\Interfaces\{86FC0C96-3FF2-4D59-9ABA-C602F213B5D2}> lsval
"UseZeroBroadcast"=dword:00000000
"EnableDeadGWDetect"=dword:00000001
"EnableDHCP"=dword:00000001
"IPAddress"=hex(7):30,00,2e,00,30,00,2e,00,30,00,2e,00,30,00,00,00,00,00
"SubnetMask"=hex(7):30,00,2e,00,30,00,2e,00,30,00,2e,00,30,00,00,00,00,00
"DefaultGateway"=hex(7):00,00
"DefaultGatewayMetric"=hex(7):00,00
"NameServer"=""
"Domain"=""
"RegistrationEnabled"=dword:00000001
"RegisterAdapterName"=dword:00000000
"TCPAllowedPorts"=hex(7):30,00,00,00,00,00
"UDPAllowedPorts"=hex(7):30,00,00,00,00,00
"RawIPAllowedProtocols"=hex(7):30,00,00,00,00,00
"NTEContextList"=hex(7):00,00
"DhcpClassIdBin"=hex(3):
"DhcpServer"="255.255.255.255"
"Lease"=dword:00000e10
"LeaseObtainedTime"=dword:412f574a
"T1"=dword:412f5e52
"T2"=dword:412f6398
"LeaseTerminatesTime"=dword:412f655a
"IPAutoconfigurationAddress"="0.0.0.0"
"IPAutoconfigurationMask"="255.255.0.0"
"IPAutoconfigurationSeed"=dword:00000000
"AddressType"=dword:00000000
Ces adresses ”“IPAddress”=hex(7):31,39,32,2e,31,36,38,2e,31,2e,31,00,00 sont à lire en prenant le deuxièmechifre de chaque champ: 192 168 1 1
8. When was the last recorded computer shutdown date/time?
system\ControlSet001\Control\Windows> lsval "Directory"=str(2):"%SystemRoot%" "ErrorMode"=dword:00000000 "NoInteractiveServices"=dword:00000000 "SystemDirectory"=str(2):"%SystemRoot%\\system32" "ShellErrorMode"=dword:00000001 "ShutdownTime"=hex(3):c4,fc,00,07,4d,8c,c4,01
Script pour convertir un REG_BINARY en date:
- convertdate.py
################################################################################ ##Convertit un timestamp windows en date lisible. ##le timestamp est le nb de ticks de 100 nanosecondes depuis le 01/01/1601 00h00 ## 1) dans la base de registre, les valeurs sont stockees en big india, on relit la valeur en hexa a l'envers ## 2) on convertit en decimal, on divise par 10 pour tomber sur des microsecondes ## 3) on calcule la date a partir du 01/01/1601 ################################################################################ from datetime import datetime,timedelta import sys ##dt= '002a59ef89b2cf01' dt =sys.argv[1] dt=''.join(reversed([dt[i:i+2] for i in range(0, len(dt), 2)])) us = int(dt,16) /10 print str(datetime(1601,1,1) + timedelta(microseconds=us))+" UTC"
# python convertdate.py c4fc00074d8cc401 2004-08-27 15:46:33.109216 UTC
9. How many accounts are recorded (total number)?
SAM\SAM\Domains\Account\Users\Names> ls Administrator Guest HelpAssistant Mr. Evil SUPPORT_388945a0
10. What is the account name of the user who mostly uses the computer?
Si on regarde le repertoire Documents and Settings, seul le compte Mr Evil semble être utilisé.
11. Who was the last user to logon to the computer?
... software\Microsoft\Windows NT\CurrentVersion\Winlogon> lsval "AutoRestartShell"=dword:00000001 "DefaultDomainName"="N-1A9ODN6ZXK4LQ" "DefaultUserName"="Mr. Evil" ...
12. A search for the name of “Greg Schardt” reveals multiple hits. One of these proves that Greg Schardt is Mr. Evil and is also the administrator of this computer. What file is it? What software program does this file relate to?
# grep -ri schardt
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/MSHist012004081620040823/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/index.dat concordant
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:oIDs[4] = "grg_schardt";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:oIDs[3] = "grgschardt";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:oIDs[2] = "g_schardt";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:oIDs[1] = "schardt_greg";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:oIDs[0] = "schardtgreg";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:<input type=hidden name=".ln" value="schardt" >
# grep -ri evil2000
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/MSHist012004081620040823/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/index.dat concordant
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:yih_aErrs[106] = "Yahoo! ID <b> mrevil2000 </b> is unavailable.";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:yih_aErrs[110] = "Yahoo! ID <b> mrevil2000 </b> is unavailable.";
root@kali:/mnt/image/Documents and Settings# grep -ri evil
Mr. Evil/Application Data/Ethereal/recent:recent.capture_file: C:\Documents and Settings\Mr. Evil\interception
Mr. Evil/Application Data/Ethereal/recent:gui.fileopen_remembered_dir: C:\Documents and Settings\Mr. Evil\
Mr. Evil/Application Data/Microsoft/Internet Explorer/brndlog.txt:08/19/2004 18:04:57 <Favorites> folder location is "C:\Documents and Settings\Mr. Evil\Favorites".
Fichier binaire Mr. Evil/Cookies/index.dat concordant
Fichier binaire Mr. Evil/interception concordant
Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/cleanup.log:CLEANUP: 16:13:55 [db] C:\Documents and Settings\Mr. Evil\Local Settings\Application Data\Identities\{EF086998-1115-4ECD-9B13-9ADC067B4929}\Microsoft\Outlook Express
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.cardz.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.codez.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.crackz.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.hackerz.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.phreakz.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.2600.programz.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/alt.binaries.hacking.beginner.dbx concordant
Fichier binaire Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/Folders.dbx concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/MSHist012004081620040823/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/MSHist012004082520040826/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/MSHist012004082620040827/index.dat concordant
Fichier binaire Mr. Evil/Local Settings/History/History.IE5/MSHist012004082720040828/index.dat concordant
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/ShowFolder[1].htm:Yahoo! Mail - mrevilrulez@yahoo.com</title>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/ShowLetter[1].htm: <b>mrevilrulez@yahoo.com</b> [<a href="/ym/Logout?YY=90802&.first=1&order=down&sort=date&pos=0&YY=90802">Sign Out</a>]
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/ShowLetter[1].htm:<tr><td class=label nowrap>To:</td><td>mrevilrulez@yahoo.com</td></tr>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/ShowLetter[1].htm: <br>Dear mrevilrulez@yahoo.com,<br><br>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/ShowLetter[1].htm: Welcome to Yahoo! Mail, a smarter way of keeping in touch. With a whopping <i>100MB of email storage, message size up to 10MB, and great virus and spam protection</i>, it's hard to believe it's <i>free!</i> Start using your new address right away: <b>mrevilrulez@yahoo.com</b></font>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/last[1].htm: <td><font face="Arial" size=-1 color="#646464"><nobr><b>Your Yahoo! ID: <font color="#000000"> mrevilrulez</font></b></font></td></tr>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/last[1].htm:<tr><td colspan=2 align=left><font face="Arial" size=-1 color="#646464"><b>Your New Yahoo! Mail Address: <font color="#000000">mrevilrulez@yahoo.com</font></b></font></td></tr>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/login[1].htm:Yahoo! Mail - mrevilrulez@yahoo.com</title>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/login[1].htm:<!-- Key=mrevilrulez#d8 chost=a38.ads.dcn.yahoo.com:57944 pls=pls2.npn.dcn.yahoo.com:98478 -->
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/login[1].htm
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/login[1].htm:
Fichier binaire Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/index.dat concordant
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:yih_aErrs[106] = "Yahoo! ID <b> mrevil2000 </b> is unavailable.";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/id_check[1].htm:yih_aErrs[110] = "Yahoo! ID <b> mrevil2000 </b> is unavailable.";
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/JIRVJY9X/wardriving[1]: <li>Hahaha this is awesome. <a href="http://www.evilscheme.org/defcon/">Airpwn</a> homepage and <a href="http://sourceforge.net/projects/airpwn">sourceforge</a>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/wbk60.tmp:such people. If you think that we are "evil people", then either go away <BR>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/ShowLetter[1].htm:Yahoo! Mail - mrevilrulez@yahoo.com</title>
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/ShowLetter[1].htm: <b>mrevilrulez@yahoo.com</b> [<a href="/ym/Logout?YY=27630&.first=1&inc=25&order=down&sort=date&pos=0&view=&head=&box=Inbox&YY=27630">Sign Out</a>]
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/id_check[1]: Congratulations, the ID<br><big><b class="yihavailid">mrevilrulez</b></big><br>is available!
Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/id_check[1]: <input class="yihbtn" type="button" onclick="if(opener){yih_insertID('mrevilrulez');}self.close();" name="continue" value="Continue Registration With This ID" style="font:bold;width:20em">
Mr. Evil/My Documents/desktop.ini:Owner=Mr. Evil
Mr. Evil/My Documents/My Music/Desktop.ini:Owner=Mr. Evil
Mr. Evil/My Documents/My Pictures/Desktop.ini:Owner=Mr. Evil
Fichier binaire Mr. Evil/NetHood/Temp on N-1a9odn6zxk4lq/target.lnk concordant
Fichier binaire Mr. Evil/NTUSER.DAT concordant
13. List the network cards used by this computer
voir question 7
14. This same file reports the IP address and MAC address of the computer. What are they?
Lire les fichiers de logs dans system32:config:
/mnt/image/WINDOWS/system32/config# file AppEvent.Evt AppEvent.Evt: data # ll | grep .Evt -rwxrwxrwx 1 root root 64K août 27 2004 AppEvent.Evt -rwxrwxrwx 1 root root 64K août 19 2004 SecEvent.Evt -rwxrwxrwx 1 root root 64K août 27 2004 SysEvent.Evt
- Logs intéressants dans AppEvent.Evt:
[Header part]
Record number : 19
Time generated : Fri Aug 20 01:04:04 2004 local (Thu Aug 19 23:04:04 2004 GMT)
Event ID : 1073742825 (no description)
Event type : 4 (Information)
Event category : 0 (None)
[Body part]
Event source : Winlogon
Computer : N-1A9ODN6ZXK4LQ
Sid : N/A
[Strings part]
String : The type of the file system is FAT32.
A disk check has been scheduled.
Windows will now check the disk.
Volume Serial Number is 1040-17EF
Windows has checked the file system and found no problems.
4745912 KB total disk space.
42680 KB in 46 hidden files.
752 KB in 165 folders.
571488 KB in 3437 files.
4130988 KB are available.
4096 bytes in each allocation unit.
1186478 total allocation units on disk.
1032747 allocation units available on disk.
Converting drive \\?\Volume{aa630442-f1ff-11d8-8a13-806d6172696f} to NTFS...
Convert will take some time to process the files on the volume.
When this phase of conversion is complete, the computer will restart.
Determining disk space required for file system conversion...
Total disk space: 4755208 KB
Free space on volume: 4130988 KB
Space required for conversion: 36508 KB
Converting file system
- Dans SysEvent.Evt:
[Header part] Record number : 6 Time generated : Fri Aug 20 00:21:51 2004 local (Thu Aug 19 22:21:51 2004 GMT) Event ID : 1007 (no description) Event type : 2 (Warning) Event category : 0 (None) [Body part] Event source : Dhcp Computer : N-1A9ODN6ZXK4LQ Sid : N/A [Strings part] String : 0010A4933E09 String : 169.254.242.213 ... Record number : 112 Time generated : Thu Aug 26 17:07:44 2004 local (Thu Aug 26 15:07:44 2004 GMT) Event ID : 2147483668 (no description) Event type : 2 (Warning) Event category : 0 (None) [Body part] Event source : Print Computer : N-1A9ODN6ZXK4LQ Sid : S-1-83886080-18 (unresolved) [Strings part] String : HP LaserJet 2100 PCL6 String : Windows NT x86 String : Version-3 String : UNIDRV.DLL, UNIDRVUI.DLL, HPLJ21P6.GPD, UNIDRV.HLP, PCL5ERES.DLL, PCLXL.DLL, PCLXL.GPD, P6FONT.GPD, PJL.GPD, P6DISP.GPD, TTFSUB.GPD, UNIRES.DLL, STDNAMES.GPD
15. An internet search for vendor name/model of NIC cards by MAC address can be used to find out which network interface was used. In the above answer, the first 3 hex characters of the MAC address report the vendor of the card. Which NIC card was used during the installation and set-up for LOOK@LAN?
Le fichier de conf de Look@Lan est irunin.ini:
/mnt/image/Program Files/Look@LAN# cat irunin.ini [Config] ConfigFile=C:\Program Files\Look@LAN\irunin.dat LanguageFile=C:\Program Files\Look@LAN\irunin.lng ImageFile=C:\Program Files\Look@LAN\irunin.bmp LangID=9 IsSelective=0 InstallType=0 [Variables] %LANHOST%=N-1A9ODN6ZXK4LQ %LANDOMAIN%=N-1A9ODN6ZXK4LQ %LANUSER%=Mr. Evil %LANIP%=192.168.1.111 %LANNIC%=0010a4933e09 ...
16. Find 6 installed programs that may be used for hacking.
Pour savoir quelles applis sont sur le système, il est possible de
- lister les applis désinstallables
- lister les hives dans HKLM/software
- lister les hives software des différents susers
- lister les userassist
- lister les MRU
- Lister les applis désinstallables:
la ruche: HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall\
software\Microsoft\Windows\CurrentVersion\Uninstall> ls
123 Write All Stored Passwords
AddressBook
Anonymizer
Branding
Cain & Abel v2.5 beta45
Connection Manager
CuteFTP
CuteHTML
DirectAnimation
DirectDrawEx
Ethereal
Faber Toys_is1
Fontcore
Forte Agent
ICW
IE40
IE4Data
IE5BAKEX
IEData
Look@LAN_1.0
Microsoft NetShow Player 2.0
mIRC
MobileOptionPack
MPlayer2
NetMeeting
Network Stumbler
OutlookExpress
PCHealth
SchedulingAgent
WinPcapInst
{350C97B0-3D7C-4EE8-BAA9-00BCB3D54227}
{6C31E111-96BB-4ADC-9C81-E6D3EEDDD8D3}
- Listing de HKLM\Software:
software\> ls Anonymizer Bar Anonymizer Plugin Bogosoft C07ft5Y Classes Clients Gemplus GlobalSCAPE Inc. Look@LAN Microsoft NeoMagic ODBC Policies Program Groups Schlumberger Secure Windows 3.1 Migration Status
- Listing des cles USERS:
NTUSER.DAT\Software> ls AnalogX Bogosoft Borland Cain Forte GlobalSCAPE Intel Microsoft mIRC Netscape Policies
- Lister les userassist:
la clé: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist> ls
{5E6AB780-7743-11CF-A12B-00AA004AE837}
{75048700-EF1F-11D0-9888-006097DEACF9}
Il faut ROT13 le contenu des ces deux clés.
- Lister les MRU:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\StreamMRU
Les streamMRU conservent les paramètres d'affichage des dossiers.
RunMRU: NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU> lsval "a"="www.cnn.com\\1" "MRUList"="dcba" "b"="cmd\\1" "c"="www.google.com\\1" "d"="telnet\\1"
17. What is the SMTP email address for Mr. Evil?
Documents and Settings/Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/id_check[1]
- Interface yahoo mail du compte mrevilrulez:
Documents and Settings/Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/PN0J7OQM/ShowLetter[1].htm
- Avec
grep -ri @yahoo.com
On trouvera le mail de confirmation de creation de compte
Documents and Settings/Mr. Evil/Local Settings/Temporary Internet Files/Content.IE5/HYU1BON0/last[1].htm
18. What are the NNTP (news server) settings for Mr. Evil? \\ Après un grep -ri nntp sur l'image, on trouve des fichiers utilisés par les applis outlook-express et agent.
- La conf de agent est dans AGENT.INI:
/mnt/image/Program Files/Agent/Data# cat AGENT.INI ;AGENT.INI ; ;For information about the settings in this file, ;search for AGENT.INI in the online help. [Profile] Build="32.560" FullName="Mr Evil" EMailAddress="whoknowsme@sbcglobal.net" EMailAddressFormat=0 ReplyTo="" Organization="N/A" DoAuthorization=1 SavePassword=1 UserName="whoknowsme@sbcglobal.net" Password="84106D94696F" SMTPLoginProtocol=2 SMTPUsePOPLogin=0 SMTPUserName="whoknowsme@sbcglobal.net" SMTPSavePassword=1 SMTPPassword="84106D94696F" IsRegistered=0 IsRegistered19=0 IsLicensed=3 Key="" EnableSupportMenu=0 [Servers] NewsServer="news.dallas.sbcglobal.net" MailServer="smtp.sbcglobal.net" POPServer="" NNTPPort=119 SMTPPort=25 POPPort=110 SMTPServerPort=25 [Groups] LastUpdate="25.August.2004 15:57:30 hrs" RefreshMode=0 RecordGaps=0
En ouvrant les autres fichiers, on retrouve des extraits de news.
- Outlook Express:
Les comptes de news sont stockés dans:
/mnt/image/Documents and Settings/Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express# ll
total 9,2M
-rwxrwxrwx 2 root root 203K août 20 2004 alt.2600.cardz.dbx
-rwxrwxrwx 2 root root 139K août 20 2004 alt.2600.codez.dbx
-rwxrwxrwx 2 root root 459K août 20 2004 alt.2600.crackz.dbx
-rwxrwxrwx 2 root root 587K août 20 2004 alt.2600.dbx
-rwxrwxrwx 2 root root 459K août 20 2004 alt.2600.hackerz.dbx
-rwxrwxrwx 2 root root 75K août 20 2004 alt.2600.moderated.dbx
-rwxrwxrwx 2 root root 267K août 20 2004 alt.2600.phreakz.dbx
-rwxrwxrwx 2 root root 203K août 20 2004 alt.2600.programz.dbx
-rwxrwxrwx 2 root root 587K août 20 2004 alt.binaries.hacking.beginner.dbx
-rwxrwxrwx 2 root root 75K août 20 2004 alt.binaries.hacking.computers.dbx
Documents and Settings/Mr. Evil/Local Settings/Application Data/Identities/{EF086998-1115-4ECD-9B13-9ADC067B4929}/Microsoft/Outlook Express/
19. What two installed programs show this information?
voir question 17
20. List 5 newsgroups that Mr. Evil has subscribed to?
voir question 17
21. A popular IRC (Internet Relay Chat) program called MIRC was installed. What are the user settings that was shown when the user was online and in a chat channel?
- Dans Program Files/mirc/mirc.ini:
... [mirc] user=Mini Me email=none@of.ya nick=Mr anick=mrevilrulez host=Undernet: US, CA, LosAngelesSERVER:losangeles.ca.us.undernet.org:6660GROUP:Undernet ...
22. This IRC program has the capability to log chat sessions. List 3 IRC channels that the user of this computer accessed.
Voir dans le repertoire de logs de mirc.
23. Ethereal, a popular “sniffing” program that can be used to intercept wired and wireless internet packets was also found to be installed. When TCP packets are collected and re-assembled, the default save directory is that users \My Documents directory. What is the name of the file that contains the intercepted data?
Deux IP sont sur le réseau local:
- 192.168.254.2 (la victime)
- 192.168.254.3 (MrEvil, le seul paquest ayant cette @ source est un paquet de diffusion SMB pour annoncer le nom du workgroup du pc…EVIL)
(voir Endpoints ou Conversations dans wireshark)
24. Viewing the file in a text format reveals much information about who and what was intercepted. What type of wireless computer was the victim (person who had his internet surfing recorded) using?
192.168.254.2 est un windows CE.
25. What websites was the victim accessing?

26. Search for the main users web based email address. What is it?
27. Yahoo mail, a popular web based email service, saves copies of the email under what file name?
28. How many executable files are in the recycle bin?
Dans le recycler:
/mnt/image/RECYCLER/S-1-5-21-2000478354-688789844-1708537768-1003# ll total 12M -rwxrwxrwx 1 root root 2,1M août 25 2004 Dc1.exe -rwxrwxrwx 1 root root 1,3M août 27 2004 Dc2.exe -rwxrwxrwx 1 root root 433K août 27 2004 Dc3.exe -rwxrwxrwx 1 root root 8,1M août 27 2004 Dc4.exe -rwxrwxrwx 1 root root 65 août 25 2004 desktop.ini -rwxrwxrwx 1 root root 3,2K août 27 2004 INFO2
Renseignements pris, les fichiers Dc1.ext portent leurs anciennes extensions, on a donc nos fichiers exe. Cependant, leurs noms et autres infos sont stockées dans le fichier INFO2.
/usr/local/bin# rifiuti /mnt/image/RECYCLER/S-1-5-21-2000478354-688789844-1708537768-1003/INFO2 Recycle bin file: '/mnt/image/RECYCLER/S-1-5-21-2000478354-688789844-1708537768-1003/INFO2' Version: 5 Index Deleted Time Gone? Size Path 1 2004-08-25 18:18:25 No 2160128 C:\Documents and Settings\Mr. Evil\Desktop\lalsetup250.exe 2 2004-08-27 17:12:30 No 1325056 C:\Documents and Settings\Mr. Evil\Desktop\netstumblerinstaller_0_4_0.exe 3 2004-08-27 17:15:26 No 442880 C:\Documents and Settings\Mr. Evil\Desktop\WinPcap_3_01_a.exe 4 2004-08-27 17:29:58 No 8460800 C:\Documents and Settings\Mr. Evil\Desktop\ethereal-setup-0.10.6.exe
29. Are these files really deleted?
:/
30. How many files are actually reported to be deleted by the file system?
31. Perform a Anti-Virus check. Are there any viruses on the computer?
Réponses
images dd
Outils
- /usr/share/regripper/rip.pl, regripper (windows)
- hivexget hivexml hivexsh